Brute Force Attacks - what are they?
What are brute force attacks?
Brute force attacks are trial-and-error attempts to crack an encryption using a large number of combinations. These can be used to guess passwords, encryption keys, API keys or SSH logins. These attacks are often carried out with the help of botnets or scripts to automate the entire process. It is a relatively easy and straightforward method which does not require advanced knowledge on the attacker’s part.
Are brute force attacks effective?
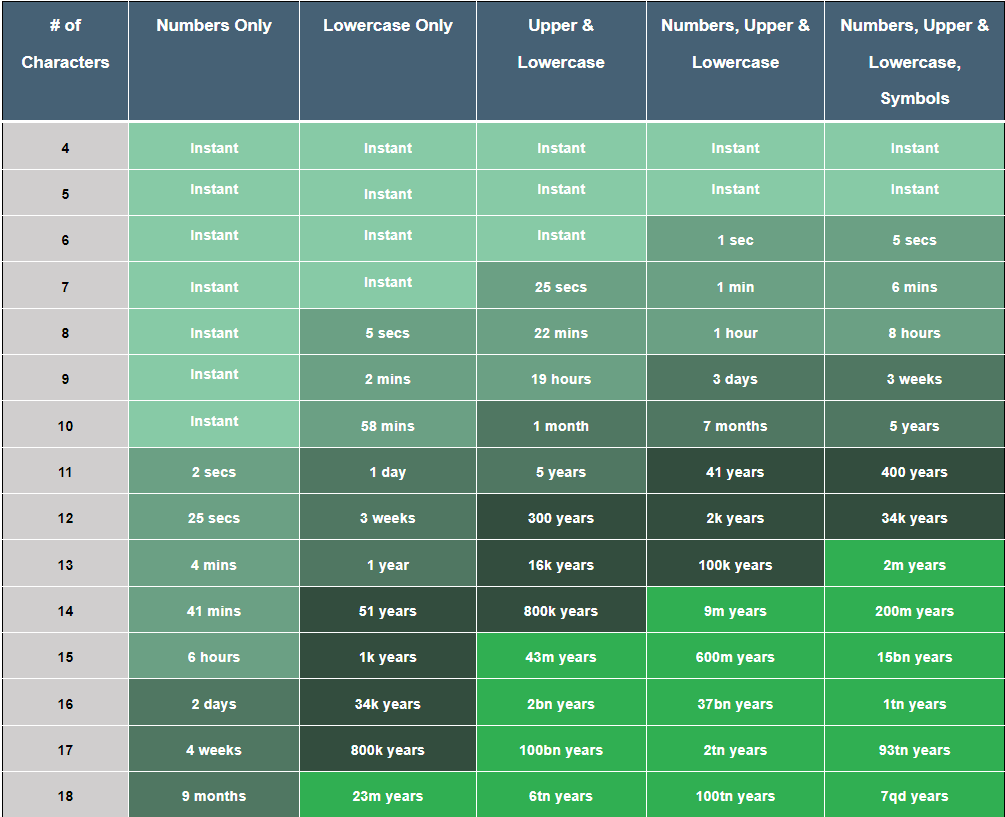
It really depends on the complexity of passwords used. Brute force attacks aren’t the most efficient of attacks as they can take a very long time to crack passwords. This is why most websites have a minimum length and special character requirements for passwords when you first create your account. Well-crafted passwords can take anywhere from 7 years of continuous processing....if the attacker has a system which can send 15 million requests every second! However, this time can be reduced by social engineering or other methods which would narrow down the possibilities of the password. Eitherway, it is still important to protect your websites from brute force attacks.
Time to Brute Force a password
How can you protect yourself?
There are few methods which can be implemented by website owners to protect themselves.
- Mandate a minimum length of 12 characters for their website passwords that includes upper/lowercase letters, numbers, and special characters.
- Lock accounts for a certain length of time after multiple failed attempts. Also add a delay of about 2-5 seconds after every failed attempt.
- Use 2FA (Second Factor Authentication). However, this system alone can still be bypassed by other types of social engineering attacks and so it should be used in conjunction with other security methods.
- As users, it is important to use different passwords for different websites. If a website is compromised and the passwords used on it are leaked, at least your accounts on other websites would be safe. Hackers like to use leaded passwords across multiple accounts because people almost always re-use passwords. This is known as a credential stuffing attack.
- Users should also be careful about where they enter passwords or other important credentials lest they fall prey to phishing attempts. You should always check to see if the address you are at is correct before entering your details
How can Polaris help you?
If you are a website owner and afraid of how brute force attacks might affect you, Polaris has multiple features which would prevent brute force attacks.
- Scanning for suspicious traffic
Polaris automatically scans all incoming traffic before admitting it to your website. If incoming traffic from a specific IP is suspicious and has the characteristics of a brute force attack, it will be identified and blocked. Furthermore, previously identified and blacklisted bots on our system will also be blocked.
- Captcha Protection
If unusual activity is detected from a certain IP, a captcha challenge will be issued to the IP before they are allowed to visit the website. If the IP is a bot or a script, it would not be able to get past the challenge easily. Repeated unusual activity will result in the IP address being blocked for some amount of time.
- White-Listing
Polaris also makes it possible for only certain users to access the website. This is done by white listing the IP addresses of those users, which would prevent everyone else from accessing the site
- Geo Blocking
If you cater to specific markets only, it is possible for you to geo-block IP addresses from other countries. For example, if your website only caters to Singapore users, you can block IP addresses from other parts of the world from accessing the site.